Unlock the Future of Cybersecurity with Zero Trust
The Critical Role of Cybersecurity in Safeguarding Patient Data
Top Trends That Come with Cybersecurity Challenges in the Healthcare Sector in 2025
Understanding the key trends shaping healthcare and the cybersecurity risks they bring
Increasing trend of keeping electronic health records (EHR).
- Challenge: Cybercriminals decrypt sensitive EHRs through ransomware attacks and demand ransom.
- Impact: EHR breaches can compromise patient confidentiality and disrupt healthcare services.

Remote healthcare staff, telehealth, and the use of multiple devices
- Challenge: Attacks on remote staff aim to gain unauthorized EHR access.
- Impact: This puts patient safety at risk and disrupts healthcare operations.
Excessive use of insecure AI and chatbots by medical staff for medical texts
- Challenge: Data breaches occur due to unsecured AI and chatbots.
- Impact: PHI exposure threatens security and patient trust.
How it may disrupt your healthcare operations
Cyberattacks on healthcare systems can lead to delays in care, high recovery costs, and reputational damage, putting your operations at risk.
The Alarming Impact of Cyberattacks on Healthcare. Are You Prepared?
-
Disrupted Patient Care
Delays in treatments due to compromised systems.t
-
High Recovery Costs
Legal fees and restoring data add to expenses.
-
Reputational Damage
Data breaches harm patient and stakeholder trust.
Ensuring Secure Health Data Storage and Cloud Security

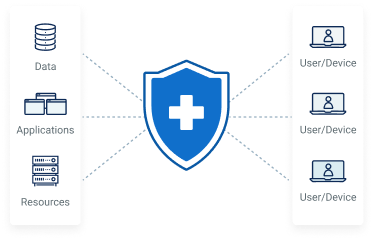
Why Choose Puredome Zero Trust for Patient Privacy?
Zero Trust Access Control
Increase Operation speed
Data Access Control for secure work from anywhere
Train Staff Regularly
Addressing Cybersecurity Regulations and Compliance in Healthcare
Understanding the legal landscape of healthcare cybersecurity is crucial for protecting data and ensuring patient safety. Recent updates emphasize stronger security measures.
HIPAA Updates
- Mandate data encryption and regular security assessments, ensuring healthcare cybersecurity compliance.
- Strengthen patient data protection and safeguard against breaches.


GDPR Compliance
- Requires comprehensive patient data protection for global organizations.
- Enforces strict security measures to prevent data breaches and ensure compliance.
Emerging Technologies and Trends 2025
in Healthcare Cybersecurity
AI Cybersecurity in Healthcare
57%
of healthcare organizations find AI effective for security.
63%
worry about protecting sensitive data with AI implementation.
AI for Threat Detection
AI is widely used for identifying and preventing security threats in healthcare.
IoT Healthcare Cybersecurity
12%
of cyberattacks targeted IoT devices in healthcare In 2022.
IoT Vulnerabilities
IoT devices pose significant security risks in healthcare.
Need for Secure Strategies
Secure IoT measures are vital to safeguard medical devices.
Blockchain Cybersecurity in Healthcare
- Blockchain ensures secure and transparent data transactions.
- Adoption is growing as healthcare seeks better data integrity and security.

The Importance of Cloud Security in Healthcare
Cloud security in healthcare is crucial as cloud-based systems in healthcare offer scalability but demand robust protection for patient data.
Protecting Sensitive Data
Cloud security ensures patient information stays encrypted and secure, safeguarding sensitive healthcare data.
Ensuring Compliance
Secured cloud-based healthcare data management systems help meet HIPAA requirements, avoiding breaches and penalties.
Mitigating Data Breach Risks
Encryption, access controls, and MFA in cloud security prevent unauthorized access to healthcare data.
Improving Access & Collaboration
Cloud-based systems enable anytime, anywhere data access for better care and privacy protection.
Addressing Healthcare Data Security Challenges
Cloud security reduces system vulnerabilities and third-party risks in healthcare data management.
Benefits of Adopting ZTNA in Healthcare
Enhanced Patient Data Protection
Improved Regulatory Compliance
Reduced Risk of Cyberattacks
Compatibility with Remote Healthcare
The Role of Third-Party Vendors in Healthcare Cybersecurity
Risks Posed by Third-Party Vendors
- Vendors access systems, risking electronic health records, patient information, and healthcare data security.
- Non-compliant vendors expose vulnerabilities, compromising healthcare security.
Strategies for Mitigation
- Use a vendor selection process to evaluate security and risks.
- Add strict cybersecurity requirements to contracts to protect health information.
EHR Security Protecting Patient Data in Healthcare
Protect Electronic Health Records (EHR) and Electronic Medical Records (EMR) by using advanced strategies to secure sensitive patient data.

EHR Security Measures
Use encryption, access controls, and audits to safeguard electronic PHI from breaches.

EHR Database Protection
Safeguard the EHR database and PHI in electronic form using secure storage and backups.

Integrated Electronic Health Records
Ensure system integration with strong security to prevent unauthorized data sharing.

EHR Compliance
Ensure compliance to protect the Electronic Health Records Dataset and ePHI.
Read our Customer Stories
Your best cybersecurity
experience awaits.
Get 5 individual VPN accounts at the lowest price ever.



