- Product
-
Solution
-
By Industry
Cybersecurity solutions tailored to your industry’s needs.
-
- Resources
-
Books
Our ultimate guides and playbooks
Solution Briefs
Overview of PureDome’s functionality
-
Quizzes
Assess your cybersecurity readiness
Case Studies
PureDome customer success stories
Newsletter
Subscribe to the PureDome newsletter
-
- About Us
- Partner
- Pricing
- Download
How Does Device Posture Check Help Enhance Network Security?
-
Aiman Ikram
-
30 Jan 2024
- 6 min read


As hackers are getting smarter, keeping your network safe is super important. That's why PureDome came up with Device Posture Check (DPC). It's like a security guard for your network, making sure only safe devices can get in. In this blog, we'll talk all about DPC: what it does, where it came from, and why it's important for you.
What is DPC Security?
DPC security is about checking the condition of devices before letting them connect to your network. It ensures that devices have the necessary security measures in place, like updates and antivirus software. If everything looks good, the device can join the network. If not, DPC blocks it, keeping your network safe from potential threats. It's like having a digital bodyguard for your network, protecting it from cyber troublemakers.
What Problem Does it Solve?
Modern organizations operate in an environment characterized by remote work, Bring Your Own Device (BYOD) policies and an ever-expanding digital landscape. While these trends offer unprecedented flexibility and efficiency, they also introduce a slew of security challenges. Employees accessing sensitive corporate data from various devices, including personal smartphones, tablets, and laptops, create potential entry points for cyberattacks.
The core problem Device Posture Check addresses is the need to ensure that only secure and compliant devices can access your network. Without such stringent checks, your organization becomes susceptible to various threats, including malware, data breaches, and unauthorized access.
Why Use Device Posture Check?
The journey to develop the Device Posture Check feature was propelled by several factors, primarily driven by the evolving threat landscape and the changing dynamics of remote work:
-
Rising Cyber Threats:
The cybersecurity landscape has witnessed a surge in sophisticated cyber threats, with hackers constantly evolving their tactics. PureDome recognized the pressing need to stay one step ahead of these threats.
-
Remote Work Proliferation:
The global shift toward remote work, accelerated by recent events, highlighted the importance of securing devices accessing corporate resources from diverse locations.
-
BYOD Challenges:
The trend of employees using their personal devices for work introduced a new layer of complexity. Managing the security of these devices and ensuring compliance with organizational policies became paramount.
-
Data Protection Regulations:
Stringent data protection regulations and compliance requirements necessitated a robust solution to control and monitor device access to sensitive data.
Benefits of DPC Security for Businesses
Now that we understand the catalyst behind the creation of Device Posture Check, let's delve into the tangible value it adds for users and organizations:
-
Enhanced Security:
Device Posture Check serves as the guardian of your network, meticulously inspecting connecting devices. By verifying compliance with predefined security policies, it significantly reduces the risk of malware infections, unauthorized access, and data breaches.
-
Compliance Assurance:
In an era of stringent data protection regulations, Device Posture Check ensures that your organization remains compliant. It helps enforce security standards mandated by regulatory bodies, providing assurance that sensitive data is accessed only by authorized users.
-
BYOD Compatibility:
The feature seamlessly integrates with Bring Your Own Device (BYOD) policies, assuring organizations that personally-owned devices meet corporate security standards. This compatibility empowers employees to use their devices for work without compromising security. It also offers prompt detection of tampered devices
-
Precise Device Control:
Device Posture Check rules are versatile and work across various operating systems. Criteria include anti-virus presence, certificates, disk encryption, and more, ensuring precise device control.
-
Secure Remote Workforces:
As remote work becomes the new norm, Device Posture Check aligns perfectly with the need for secure remote access. It runs in parallel with encryption provided by cloud gateways, creating a secure environment for employees to access corporate resources remotely.
-
Move Forward In Zero Trust Network Access Strategy:
Providing admins control over devices in addition to users helps them move forward in their Zero TrusIt strategy which asks for more granular controls on network access.
What Industries Is DPC Most Useful For?
-
Healthcare Institutions:
To ensure that devices accessing patient data meet stringent security standards, in line with regulations like HIPAA.
-
Financial Institutions:
Given the sensitive nature of financial data, banks, insurance companies, and other financial entities need to ensure a high level of device security.
-
Government Agencies:
To protect state secrets, citizen data, and other sensitive information.
-
Tech and Software Companies:
Especially those dealing with customer data or intellectual property.
-
Educational Institutions:
To protect academic records, research data, and ensure the integrity of online examinations.
-
E-commerce Businesses:
To safeguard customer data, transaction details, and financial information.
-
Large Enterprises:
With a vast number of employees and devices, maintaining a consistent security standard is crucial.
DPC Security Best Practices
Regular Updates: Make sure all devices have the latest software updates and patches installed to fix any known security issues.
Antivirus Software: Install and regularly update antivirus software on all devices to protect against viruses and malware.
Firewall Protection: Enable and configure firewalls on devices to control incoming and outgoing network traffic and block unauthorized access.
Strong Passwords: Use strong, unique passwords for devices and regularly change them to prevent unauthorized access.
Network Segmentation: Divide your network into separate segments to limit the spread of threats and protect critical assets from unauthorized access.
DPC Security vs. Traditional Security Methods
DPC security focuses on checking the security posture of individual devices before allowing them to connect to the network. It offers granular control and blocks non-compliant devices. Traditional security methods, on the other hand, often rely on perimeter defenses and may lack visibility into individual devices. They protect the entire network perimeter and may allow access to non-compliant devices.
|
DPC Security |
Traditional Security Methods |
|
Checks device posture before connection |
Relies on perimeter defenses like firewalls |
|
Focuses on individual device security |
Protects entire network perimeter |
|
Requires devices to meet specific criteria |
Often relies on network-wide security protocols |
|
Offers granular control over access |
May lack visibility into individual devices |
|
Blocks non-compliant devices from access |
May allow access to non-compliant devices |
Device Posture Compliance Parameters
Device posture check rules are designed to allow access only from secured and recognized Windows, macOS, iOS, and Android mobile devices. This ensures a secure and controlled access environment for your organization.
-
Antivirus:
Verify whether the device has the organization’s preferred antivirus software installed.
-
Disk Encryption:
Verify if the disk is encrypted.
-
File Exists:
Verify the presence of a file necessary for maintaining the proper security posture on the device.
-
Process Running:
Verify whether a specific process is currently running on the device.
-
Certification:
Verify the presence of a specific certification on the device.
-
Operating System Version:
Verify that the device is using an excepted OS version (equal to and/ or higher than).
-
Windows Registry:
Verify the existence of a specific registry path or value in the device’s Windows Registry.
Implementing Device Posture Before and After Connection
Enhancing device security is crucial, as attackers can exploit vulnerabilities before or during network access. With PureDome DPC, you can conveniently assess device security before connecting to the network and on a custom schedule for continuous protection, ensuring round-the-clock device security.
How to Use PureDome Device Posture Check?
Create Device Posture Check Profiles
- To add a Device Posture Check profile, click the Device tab in the PureDome console on the left side.
- Click Posture Check.
- Click Add profile.
- Enter a Posture check profile name.
- Select the team(s) that should comply with the posture check profile.
Note: The Device Posture Check profiles will be applied to all the team members added to a team. - Select the suitable Runtime Schedule.
Note: The Device Posture Check profile can be verified either while a team member is connected to PureDome or with every connection to PureDome.
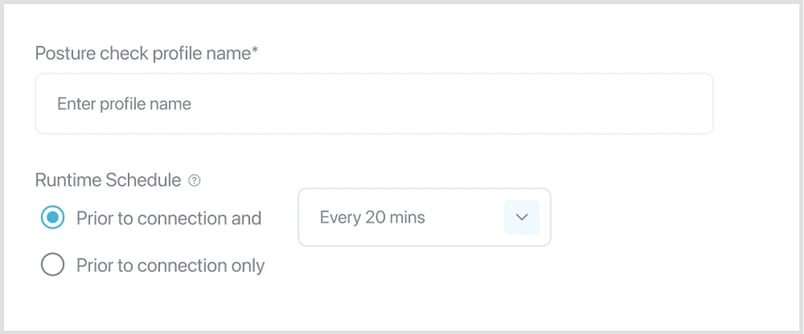
Define posture check specific to each OS
Admins have an option to create different profiles for different operating systems within the same setup or generate separate profiles for each OS.
Each OS profile can have one or more rules which must be met in order to gain access to the PureDome network.
Windows
- Click Add OS to profile.
- Select and define rules.
-
Antivirus:
PureDome will verify whether the device has the organization’s preferred antivirus software installed.
-
File-Exists:
PureDome will verify the presence of a specific file in a specific path.
-
Disk Encryption:
PureDome will verify whether the OS hard-drive is encrypted.
-
Certificate:
PureDome will verify the presence of a specific certification on the device. (in the local Windows CA store).
-
Process Running:
PureDome will verify whether a specific process is currently running on the device.
-
Registry:
PureDome will verify the existence of a specific registry path or value in the device’s Windows Registry.
-
Operating System Version:
PureDome will verify that the device is using an excepted OS version (equal to and/ or higher than).
-
Active Directory Association:
PureDome will verify the user's "login_domain" matches what is specified in the rule.
-
Windows Security Center:
PureDome will verify the status of the selected Firewall, or Antivirus is showing as "Good".
- Click Add rule to OS (if needed)
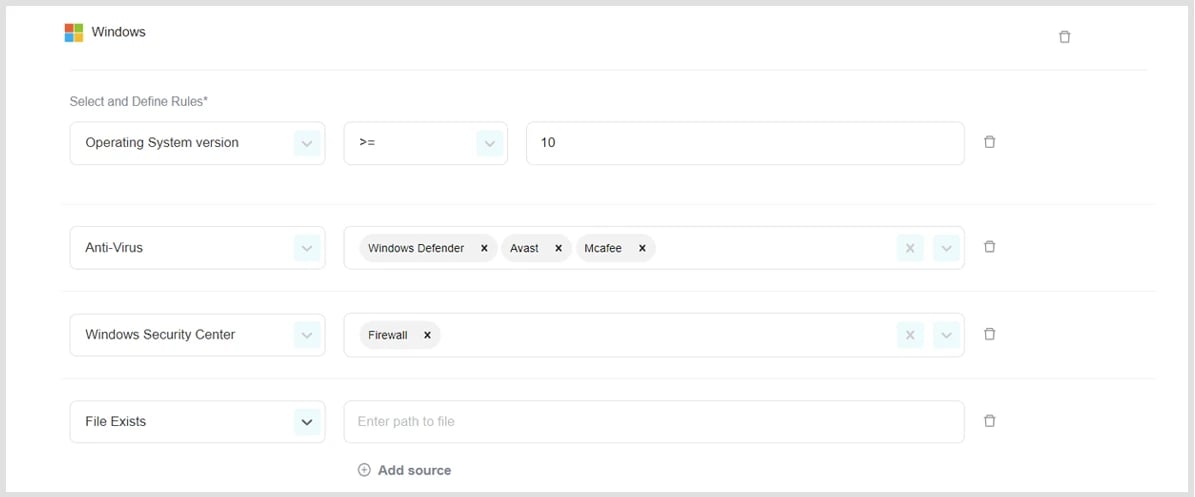
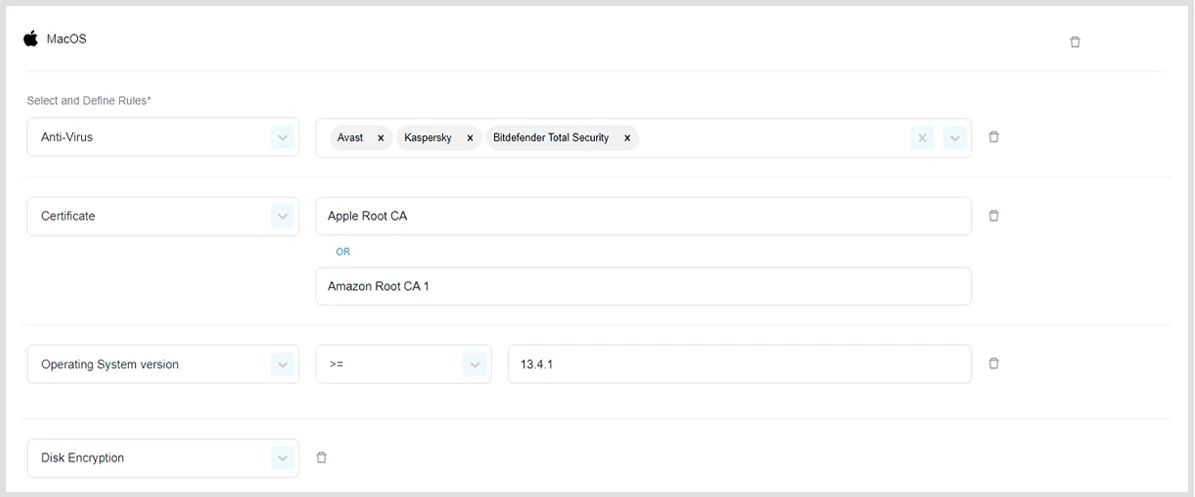
macOS
- Click Add OS to profile.
- Select and define rules.
-
Antivirus:
PureDome will verify whether the device has the organization’s preferred antivirus software installed.
-
File-Exists:
PureDome will verify the presence of a specific file in a specific path.
-
Disk Encryption:
PureDome will verify whether the OS hard-drive is encrypted.
-
Process Running:
PureDome will verify whether a specific process is currently running on the device.
-
Certificate:
PureDome will verify the presence of a specific certification on the device. (macOS Keychain).
-
Operating System Version:
PureDome will verify that the device is using an excepted OS version (equal to and/ or higher than).
- Click Add rule to OS (if needed)
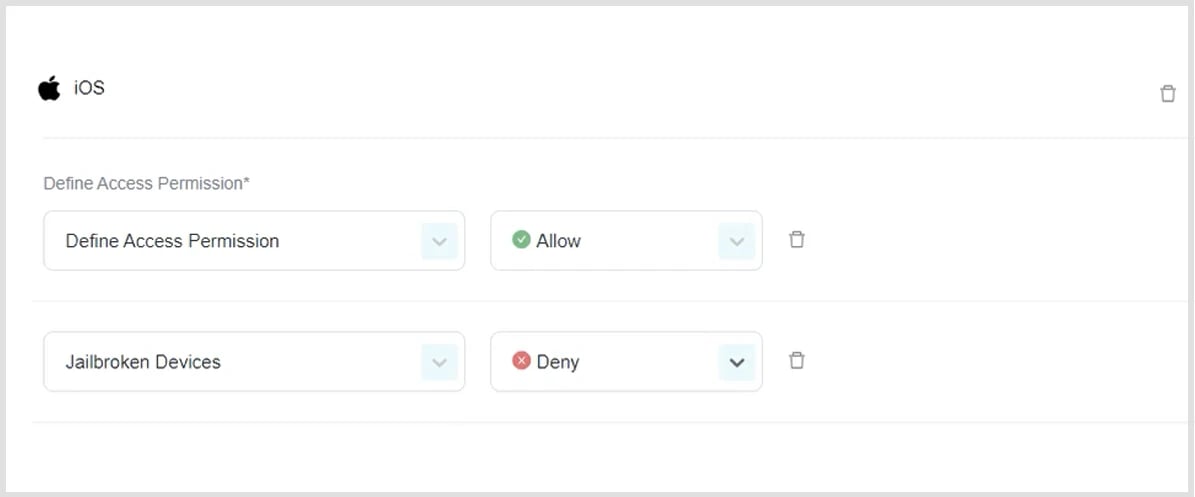
iOS
- Click Add OS to profile.
- Select and define rules.
-
Allow:
Mobile devices using the PureDome application will be allowed into the PureDome network.
-
Deny:
Mobile devices using the PureDome application will be denied access into the PureDome network.
-
Jailbroken Devices:
Jailbroken devices will either be allowed or denied access into the PureDome network.
- Click Add rule to OS (if needed)
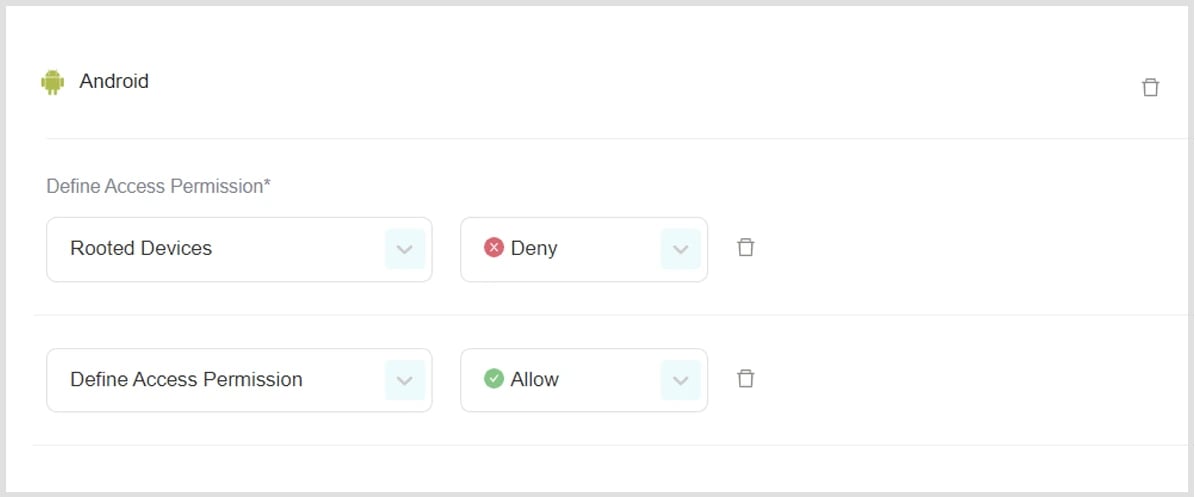
Android
- Click Add OS to profile.
- Select and define rules.
-
Allow:
Mobile devices using the PureDome application will be allowed into the PureDome network.
-
Deny:
Mobile devices using the PureDome application will be denied access into the PureDome network.
-
Rooted Devices:
Rooted devices will either be allowed or denied access into the PureDome network.
- Click Add rule to OS (if needed)
Stay up to date with the latest cybersecurity insights and best practices
Get the latest information, stories, and resources in your inbox. Subscribe for monthly updates.
Securing 1000+ Businesses Across The World