Securing 1000+ teams & business across the world
Why do you need device posture security?
You are onboarding remote workers or contractors to work on your systems and want to make sure their devices meet your key security requirements
Your employees can use personal devices or devices owned by outside firms to access protected company resources
You’re looking to comply with global regulatory compliance frameworks like HIPAA, PCI DSS, NIST, ISO/IEC 27001, GDPR, or FERPA, which require users to undergo device health or posture checks
Your organization does not have an MDM solution, and you want to ensure that each device meets your security requirements before it can access your key assets
PureDome’s Device Posture Checks in action
Making device posture a consistent and easily managed part of your secure access policies.
Enhanced Overall Security
Dramatically reduce the risk of vulnerabilities, malware, or breaches by ensuring that only secure and healthy devices connect to the corporate network. Continuously verify endpoint trust through Adaptive Access Controls to restrict devices when their security posture changes from the policies you’ve set in place - until they are compliant again.
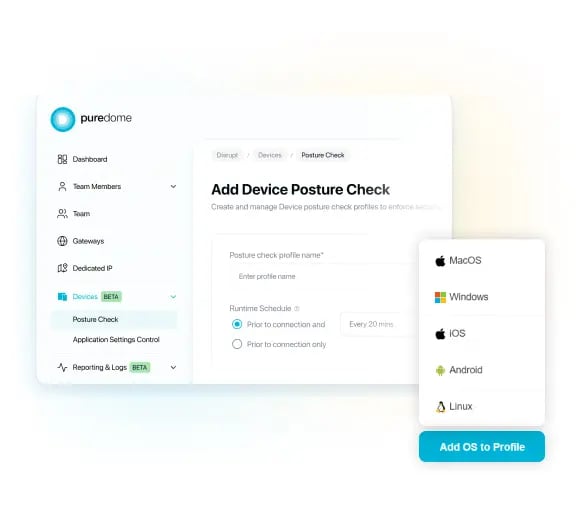
Easy to Manage Policies Across Multiple OS
Create multiple posture profiles for your teams across 5 major operating systems with an easy-to-use interface that lets you define how frequently Puredome needs to check users for their device security posture based on a runtime schedule.
Supported operating systems with app support

Consistent Device Security Posture Assessment
Establish device trust before allowing access to corporate applications by enabling administrators to enforce a uniform security policy across all devices so non-compliant devices are blocked at the time of authentication and your organization maintains a consistent security posture through and through.
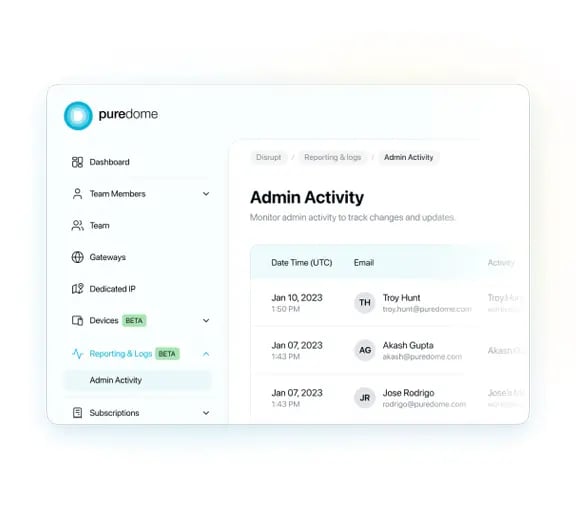
Easy Reporting and Management
Enable administrators to maintain an inventory of all devices accessing your resources so they get a clear view of device compliance across the organization to aid in security audits, monitor security policies, and spot anomalous login activities.

Reduced IT Overhead
Reduce the manual workload on IT teams with automated checks that empower users with self-remediation so they can update their devices to meet the corporate security policies set up by administrators, causing fewer IT tickets to be raised as IT ensures their endpoint fleet is consistently compliant.
Feature Details

Number of supported profiles

Supported OS
- Mac
- Windows
- iOS
- Android
- Linux

Runtime Scheduling Frequency
- Prior to connection
- Every 20 minutes
- Every 40 minutes
- Every 60 minutes
Supported Rules
- Anti-virus
- Certificate
- Operating System Version
- Disk Encryption
- Block Torrenting
- File Exist
- Process Running
- Registry
- Windows Security Center
- Active Directory Association
- Rooted devices
More features that amplify your network security

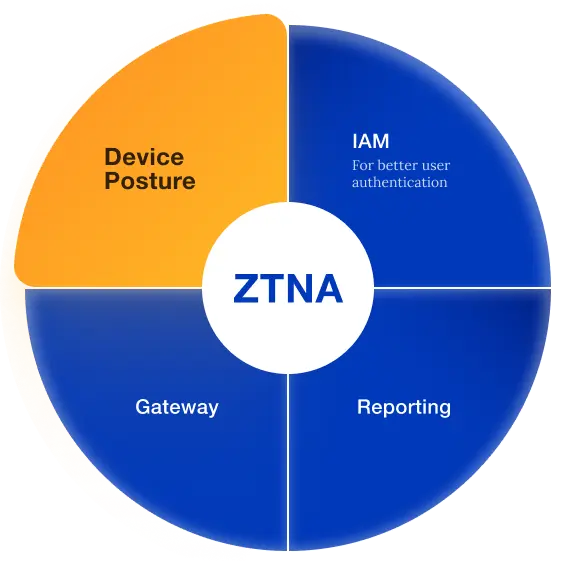
Identity Access and management
for dependable device security

Gateways
for micro-segmentation

Admin reports
for granular visibility
Ready to introduce better identity management on your network?
Frequently Asked Questions
What is a Device Posture Check (DPC), and how does it enhance network security?
It empowers administrators to enforce predefined security policies, ensuring that only compliant devices can connect to the network using the PureDome app. It enhances network security by preventing unauthorized or non-compliant devices from accessing the network, reducing the risk of security breaches.
How does DPC contribute to our network's overall security strategy?
Device Posture Check plays a crucial role in advancing your network's security strategy, especially in the context of ZTNA. It goes beyond user-based controls by allowing administrators to manage devices as well. This means you can implement more granular controls on network access, aligning with a robust security strategy.
Can users still access the network with their devices using DPC in place?
Yes, users can still access the network with their devices if they comply with the defined security policies. DPC is designed to provide a balance between security and accessibility, ensuring that compliant devices can connect seamlessly while enforcing security standards to protect the network from potential threats.
What industries is it useful for, and how?
Healthcare Institutions: To ensure that devices accessing patient data meet stringent security standards in line with regulations like HIPAA.
Financial Institutions: Given the sensitive nature of financial data, banks, insurance companies, and other financial entities need to ensure a high level of device security.
Government Agencies: To protect state secrets, citizen data, and other sensitive information.
Tech and Software Companies: Especially those dealing with customer data or intellectual property.
Educational Institutions: To protect academic records and research data and ensure the integrity of online examinations.
E-commerce Businesses: To safeguard customer data, transaction details, and financial information.
Large Enterprises: With a vast number of employees and devices, maintaining a consistent security standard is crucial.



-1.webp?width=864&height=418&name=cover%201%20(4)-1.webp)
.webp?width=864&height=418&name=cover%201%20(14).webp)
