- Product
-
Solution
-
By Industry
Cybersecurity solutions tailored to your industry’s needs.
-
- Resources
-
Books
Our ultimate guides and playbooks
Solution Briefs
Overview of PureDome’s functionality
-
Quizzes
Assess your cybersecurity readiness
Case Studies
PureDome customer success stories
Newsletter
Subscribe to the PureDome newsletter
-
- About Us
- Partner
- Pricing
- Download
HIPAA Omnibus Rule Explained: Key Changes, Compliance Requirements, and How to Stay Ahead
-
Aiman Ikram
-
22 May 2025
- 5 min read

Did you know the HIPAA Omnibus Rule increased penalty limits by 400%?
That stat alone is enough to make anyone dealing with patient data sit up straight. Especially when you're juggling remote teams, third-party vendors, and cloud tools. The digital health landscape has grown, and so has the scope of who’s responsible for safeguarding data. The HIPAA Omnibus Rule was the big wake-up call in 2013 that we're still feeling the effects of.
And here’s the thing—most teams are still playing catch-up.
This isn’t a history lesson. It’s a reality check for IT managers, security heads, and business owners in healthcare and adjacent fields. If you're working with sensitive health info (PHI), it's time to reassess whether your systems and people are really as locked down as you think.
Let’s dig in.
What Is the HIPAA Omnibus Rule, Really?
You might have heard it tossed around in compliance meetings or legal briefings, but here’s what it actually is. The HIPAA Omnibus Rule is a set of sweeping updates that modified the original HIPAA regulations. It clarified and expanded responsibilities for everyone involved in handling health data—not just hospitals, but also vendors, cloud providers, and remote contractors.
It’s not just about ticking boxes anymore. It’s about proactive protection.
- It expanded the definition of "business associates" to include cloud service providers and data storage firms.
- It enforced new limits on how data is shared and marketed.
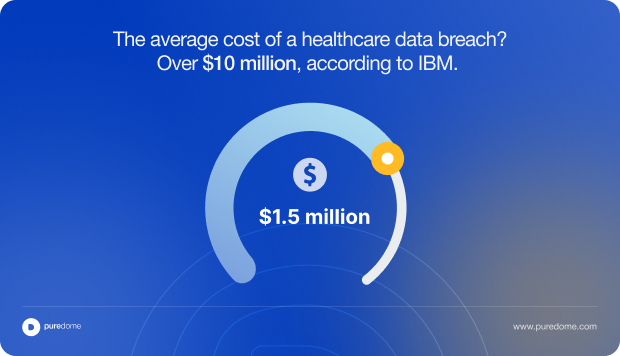
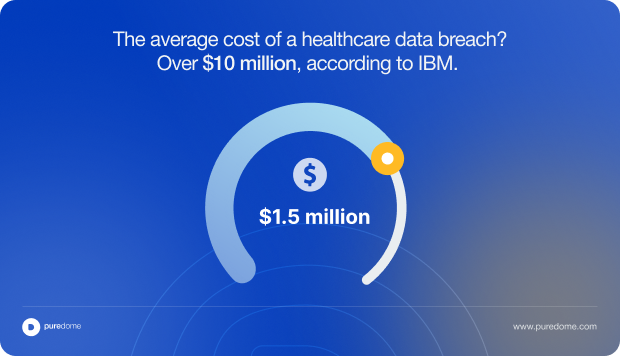
- It raised the financial stakes by increasing penalty caps to $1.5 million per violation.
- It gave patients more rights over their health data, including who sees it and where it goes.
What Changed with the HIPAA Omnibus Rule?
This wasn’t a small patch or legal clarification. This was a significant overhaul. A shift in how organizations need to view security—especially those who thought outsourcing or using SaaS platforms gave them cover.
Now, everyone in the data chain is liable.
- Business Associates must sign BAA agreements and follow HIPAA Security and Privacy Rules directly.
- Cloud services handling PHI are no longer in the gray zone. They’re in the spotlight.
- Data breach notifications are required if there's more than a low probability of compromised data.
- Use of PHI in marketing is restricted unless there's clear patient authorization.
The New Meaning of Business Associates
Here’s where it gets tricky—because the term “business associate” now includes a lot more people than you think. And if you're running any kind of tech-forward health business, that probably means you.
You can’t rely on contracts alone anymore.
- Remote IT contractors? Business associates.
- Cloud file storage platforms? Business associates.
- Analytics tools that touch PHI? Yep—business associates.
If these partners aren’t fully compliant, you’re on the hook.
HIPAA Isn’t Just a Healthcare Problem Anymore
As the digital landscape expands, so does the reach of HIPAA. It’s no longer just about hospitals, insurance companies, or doctors' offices. The Omnibus Rule made it clear—anyone handling Protected Health Information (PHI) needs to be in the compliance game. Whether you’re a tech company storing health data in the cloud, a contractor managing patient records, or a marketing firm using patient information for campaigns, you're in the mix now. That means if you're dealing with PHI, you're not just subject to the law—you're responsible for keeping it safe.
This is an issue that stretches beyond healthcare itself and impacts any business in the health-adjacent ecosystem. So, even if healthcare isn’t your primary industry, you'd better believe HIPAA compliance is still on your radar.
Read up more on the future of regulatory compliance solutions in healthcare here.
Real Compliance Requirements—Not the Checklist Version
HIPAA compliance doesn’t live in a folder on someone's desktop. It’s ongoing, operational, and—if you’re not careful—exhausting. The Omnibus Rule made that clearer than ever.
So what do you actually need to have in place?
- Risk assessments that aren’t just for audit time. They need to be ongoing.
- Encryption and access controls that extend to remote and third-party users.
- Employee training that doesn’t just happen once a year.
- Incident response plans that are real, not theoretical.
Read: HIPAA Compliance Checklist
HIPAA Omnibus Compliance Checklist
When it comes to staying compliant, checklists help—but only if they reflect real-world practices, not just policy documents. A proper HIPAA Omnibus checklist should include signed Business Associate Agreements (BAAs) with every partner handling PHI, regular risk assessments across systems and vendors, and secure remote access solutions.
Encryption—both at rest and in transit—is a must, along with role-based access controls and segmentation to limit exposure. Employee training shouldn’t be a once-a-year checkbox; it needs to be consistent and current.
You also need clear breach notification procedures, third-party vendor audits, a solid BYOD policy, and audit trails to track who accesses PHI and when. Without these essentials, your compliance plan has gaps—and gaps are where violations happen.
|
Requirement |
Description |
Responsible Party |
|
Business Associate Agreements (BAAs) |
Ensure signed BAAs with all partners handling PHI |
Legal / Compliance Lead |
|
Ongoing Risk Assessments |
Regularly assess vulnerabilities across systems and vendors |
IT / Security Team |
|
Secure Remote Access |
Use encrypted connections and access controls for remote workers |
IT Admin / Security Lead |
|
Data Encryption |
Encrypt PHI both at rest and in transit |
IT Team |
|
Access Control and Segmentation |
Restrict PHI access based on role, device, and network |
IT / System Admin |
|
Workforce Training |
Conduct regular HIPAA and security awareness training |
HR / Compliance |
|
Breach Notification Procedures |
Create and test a breach response plan, including patient notification steps |
Security / Legal / Comms |
|
Vendor Due Diligence |
Audit third-party vendors for HIPAA alignment |
Procurement / IT |
|
BYOD Policy Implementation |
Set clear rules and controls for employee-owned devices |
IT / HR |
|
Audit Trail and Activity Logs |
Maintain logs of PHI access and modifications |
IT / Compliance |
Common Gaps in HIPAA Omnibus Compliance
Even well-meaning companies fall short. Not because they don’t care, but because they don’t have visibility across devices, networks, and endpoints—especially now that so many teams are remote.
There’s a pattern to what gets missed:
- Assuming your vendors are compliant without checking or auditing them.
- Not using secure access channels for remote work.
- No clear policies for BYOD (bring your own device) setups.
- Inconsistent data storage practices between teams or departments.
The Growing Impact of HIPAA Enforcement
Enforcement is no longer rare. The Office for Civil Rights (OCR) has been stepping up, and small clinics and startups are no longer flying under the radar.
And it’s not just about fines—it’s about public trust and reputation.
- The average cost of a healthcare data breach? Over $10 million, according to IBM.
- In 2023 alone, more than 133 million healthcare records were exposed through data breaches.
- OCR now investigates every breach involving 500+ individuals.
So, How Do You Stay Ahead?
You can’t just protect the data inside your office walls. You have to protect the network as a whole—especially as more health-related work moves offsite, and more business associates enter your workflow.
This is where a tool like PureDome earns its spot.
- It offers Dedicated IPs and centralized access control, perfect for distributed teams.
- It helps ensure secure remote access without relying on potentially non-compliant ISPs or third-party VPNs.
- It enables you to segregate access based on teams or user roles, cutting exposure in case of incidents.
PureDome doesn’t just check the compliance box—it actively reduces risk.
And that’s what HIPAA Omnibus really demands.
Final Thought: Compliance Is Not a One-Time Project
If you're still treating HIPAA compliance like a task to finish and file, you're missing the point. The Omnibus Rule made it clear: security and compliance are everyday work.
But it doesn’t have to be a nightmare. With the right infrastructure, you can manage access, maintain visibility, and stay on the right side of risk—even as your team grows and shifts.
Tools like PureDome aren’t just for IT—they’re part of a proactive healthcare data strategy.
And that might be what saves you from the next headline-making breach.