
Healthcare is facing a surge in data breaches, with millions of patients' information exposed in just the first quarter of 2024. Traditional security methods are falling short, leaving medical centers vulnerable to attacks, especially with the rise of telemedicine and IoT devices.
Zero Trust Network Access (ZTNA) offers a solution by requiring all users, whether inside or outside the network, to authenticate and validate their identities before accessing sensitive data. This blog talks about the ways in which ZTNA can transform the healthcare sector to secure PHI even better.
What Is Zero Trust Network in Healthcare?
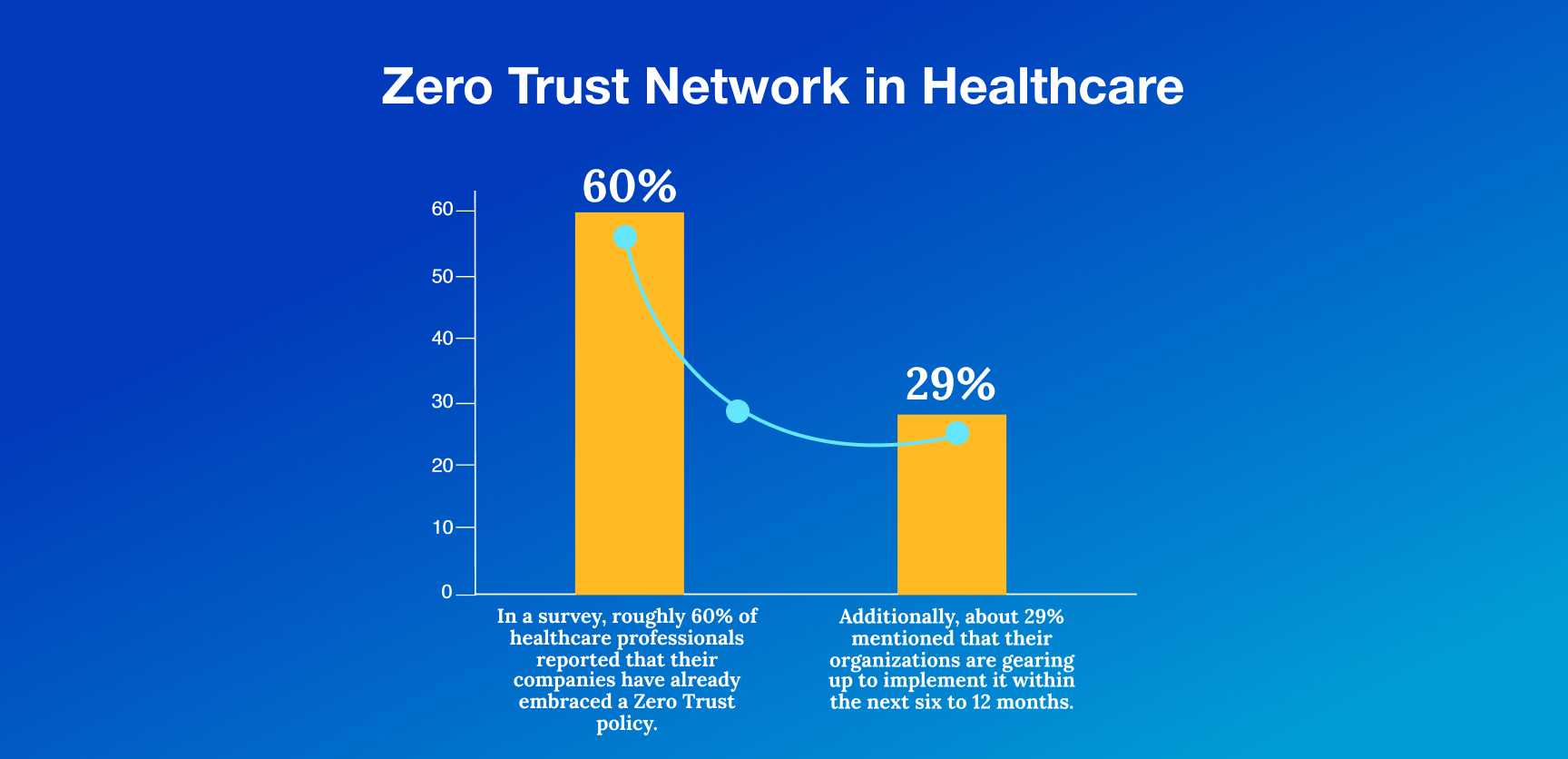
In a survey, roughly 60% of healthcare professionals reported that their companies have already embraced a Zero Trust policy. Additionally, about 29% mentioned that their organizations are gearing up to implement it within the next six to 12 months.
Zero Trust Network in healthcare is like putting your data on lockdown mode. It's a security approach where no one gets a free pass, whether they're inside or outside the network. You have to prove who you are and that your device is authorized before you can access any sensitive information. This approach is crucial in the current landscape where digital threats are constantly evolving, aiming to protect patient data from unauthorized access and potential breaches.
Healthcare Data at Risk: Key Insights
As per a Trustwave report, a single healthcare data record could fetch as much as $250 on the black market, significantly higher than the next most valuable record, which is a payment card, valued at $5.40.
Here are 3 of the biggest healthcare data breaches:
- Anthem Inc.: It is the biggest healthcare system in US. This breach affected a whopping 79 million people. Hackers got into a database with personal info like names, addresses, and Social Security numbers.
- Premera Blue Cross: It is one of the most popular not-for-profit organizations in healthcare. Around 11 million individuals were impacted. The hackers accessed records with personal details including names, birth dates, and Social Security numbers.
- UCLA Health System: This is ranked as one of America's top hospitals. The breach exposed over 4.5 million patient records.
How to Implement a Zero Trust Architecture?
For starters, begin by checking out your network, finding where it's vulnerable, and figuring out what's most important to protect. Then, split up your network into smaller chunks and only let people into the ones they really need.
Top up user IDs with extra layers like multi-factor authentication and keep an eye on who's doing what in real-time. Don't forget to lock down those endpoints and train your team to be on guard. And always stay up to date with the latest security rules and regulations.
How Zero Trust Compares with Other Cybersecurity Strategies
Zero Trust is all about being super cautious and making sure only the right people get access to sensitive information, while traditional methods rely more on keeping the threats out at the network's edge.
|
Cybersecurity Strategy |
Description |
Zero Trust |
Traditional Perimeter-Based |
|
Approach |
Verifies every user and device accessing the network, granting access based on need. |
✓ |
✗ |
|
Access Controls |
Implements strict controls, demanding authentication for every access attempt. |
✓ |
✗ |
|
Least Privilege Principle |
Limits access to only what's needed for a user's job. |
✓ |
✗ |
|
Monitoring and Detection |
Keeps a constant eye out for any unusual activities on the network. |
✓ |
✗ |
|
Endpoint Security |
Focuses on securing all devices connected to the network. |
✓ |
✗ |
Benefits of Zero Trust in Healthcare
1.Tightened Security
Zero Trust is like the security guard of healthcare networks, double-checking everyone's ID before letting them through the door. It makes sure only the right people, whether they're inside or outside the network, get access to sensitive patient data. With this approach, even if a hacker manages to slip past the gates, they'll hit another roadblock before reaching the important data.
2. Reduced Risk of Breaches
Picture Zero Trust as a fortress around patient data, with guards stationed at every entry point. By closely monitoring who's coming in and out and limiting access to only what's necessary, it significantly reduces the chances of unauthorized access. This means fewer opportunities for hackers to sneak in undetected and steal valuable PHI.
3. Compliance Assurance
It makes sure you're always following the rules, especially when it comes to patient privacy. By enforcing strict access controls and keeping detailed records of who's accessing what, it helps healthcare organizations stay on the right side of regulations like HIPAA. This not only protects patient data but also shields the organization from hefty fines and reputational damage.
4. Enhanced Endpoint Security
With Zero Trust, every device connected to the network, from computers to medical devices, gets its own bodyguard. By focusing on securing these endpoints and keeping their software up to date, it creates an extra layer of defense against cyber threats. This means fewer vulnerabilities for hackers to exploit and fewer opportunities for them to wreak havoc on the network.
5. Improved Insider Threat Management
Zero Trust doesn't just watch out for outsiders trying to break in; it keeps a close eye on what's happening inside the network too. By monitoring user behavior and keeping tabs on privileged access, it helps detect and prevent insider threats before they can cause any harm. This proactive approach to security ensures that even the folks on the inside are playing by the rules and not putting patient data at risk.
Can a Partner Help Healthcare Organizations Implement Zero Trust?
Absolutely! Partners can play a crucial role in helping healthcare organizations implement Zero Trust. Puredome offer specialized expertise and solutions tailored to enhance cybersecurity measures. They provide Zero Trust Network Access (ZTNA) solutions that authenticate and authorize users before granting access to sensitive data.
Their technology ensures that only verified individuals with the right credentials can access healthcare networks, significantly reducing the risk of data breaches and unauthorized access. Partnering with such experts can streamline the implementation process and bolster security measures effectively. To read more about PureDome in action, check out the case study on securing healthcare virtual assistants for HelloRache.